Digital Doctor
Well-known member
How secure is your forum software ?
Does your forum provider spit out code with vulnerabilities or do they have better quality control than that ?
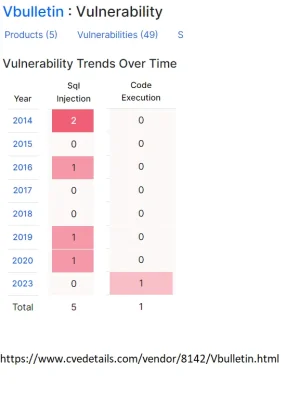
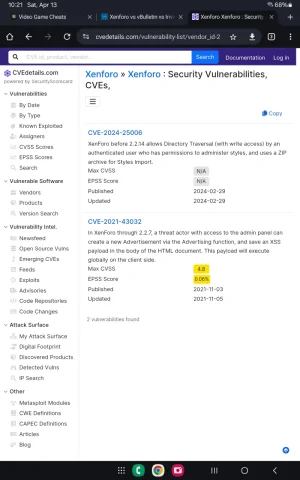
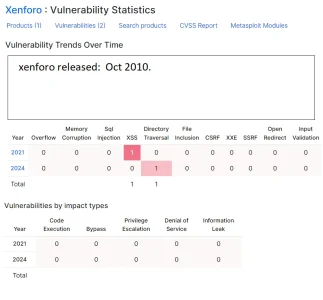
Xenforo: (source: https://www.cvedetails.com/vendor/25815/Xenforo.html )
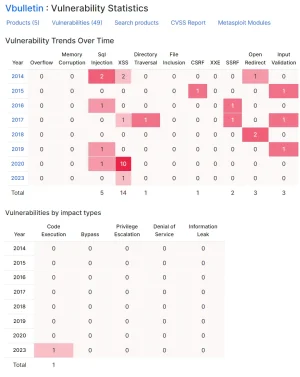
vBulletin: source: https://www.cvedetails.com/vendor/8142/Vbulletin.html
Invision Coummunity / source: https://www.cvedetails.com/vendor/21021/Invisioncommunity.html
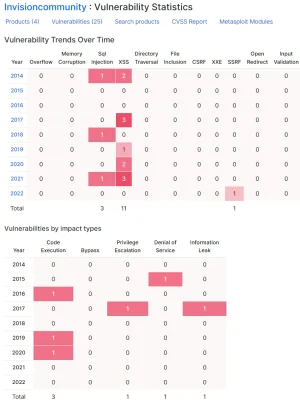
I'll let the numbers speak for themselves.
Does your forum provider spit out code with vulnerabilities or do they have better quality control than that ?
Xenforo: (source: https://www.cvedetails.com/vendor/25815/Xenforo.html )

vBulletin: source: https://www.cvedetails.com/vendor/8142/Vbulletin.html

Invision Coummunity / source: https://www.cvedetails.com/vendor/21021/Invisioncommunity.html

I'll let the numbers speak for themselves.