Helmuts
New member
Good morning,
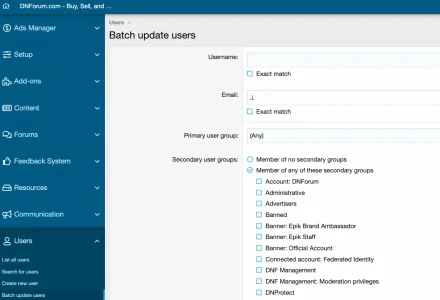
What is the recommended process on cleaning user accounts? Last April I acquired 2 old forums (est. in 2001 and 2004) and need to clean the users so that we can start sending monthly DMs (newsletters with industry updates) to our users, and maintaining low email bounce-rate.
Received an interesting suggestion:
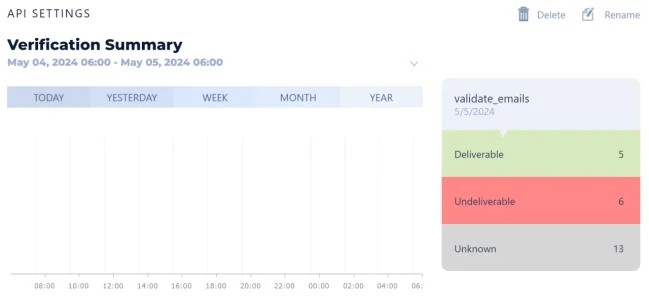
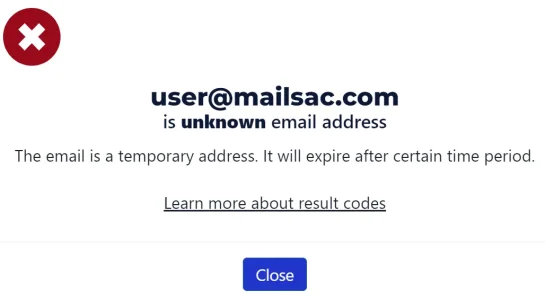
1 thing I am not prepared to do - removing users who haven't looged in the forum within the last 1 year (or, even 5 years). I keep seeing old members returning once they learn that a forum is in good hands now. .. my main issue is a forum with 530k users > test email blast showed around 50% bounce-rate (and we stopped it, of course).
Thank you for sharing your expertease. H
What is the recommended process on cleaning user accounts? Last April I acquired 2 old forums (est. in 2001 and 2004) and need to clean the users so that we can start sending monthly DMs (newsletters with industry updates) to our users, and maintaining low email bounce-rate.
Received an interesting suggestion:
you don't need to delete those users, just disable email sending to those users after you determine and clean your users' email addresses.
1 thing I am not prepared to do - removing users who haven't looged in the forum within the last 1 year (or, even 5 years). I keep seeing old members returning once they learn that a forum is in good hands now. .. my main issue is a forum with 530k users > test email blast showed around 50% bounce-rate (and we stopped it, of course).
Thank you for sharing your expertease. H